
Although alarming at first glance, Bybit responded quickly, resolving the issue with no broader implications to the platform or other users.
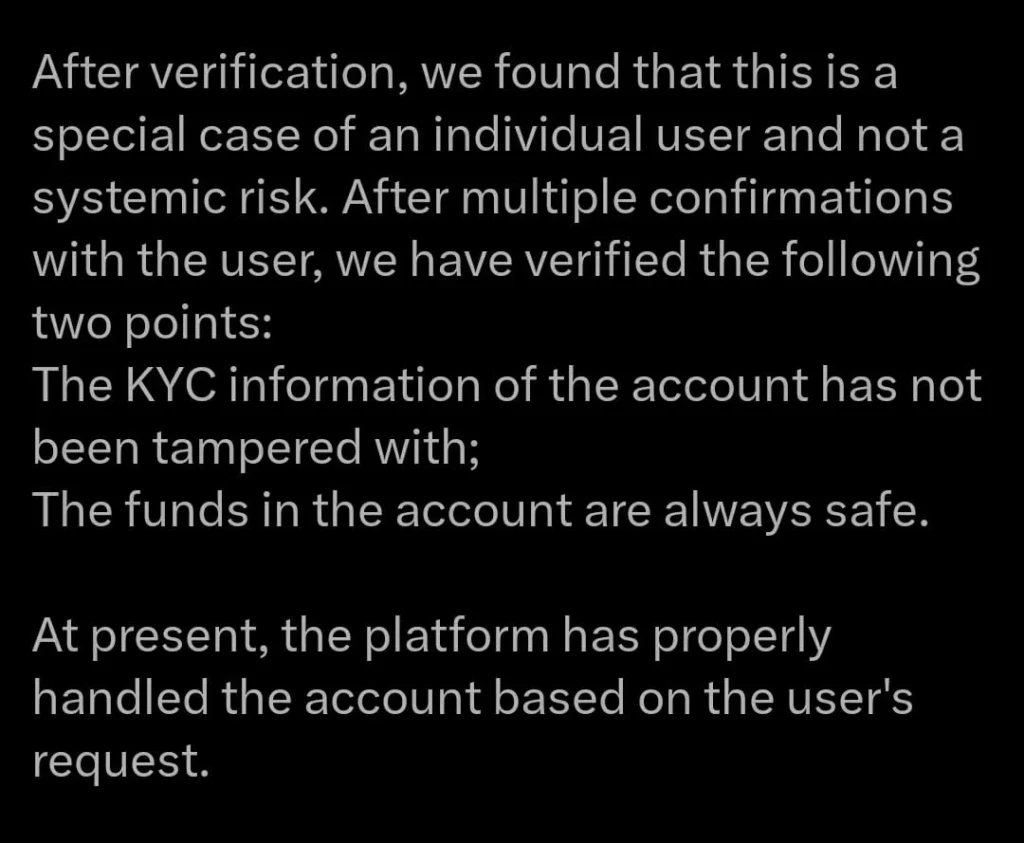
Bybit’s reaction to the Apple ID login irregularity was immediate and decisive. The company mobilized key personnel, including Chief Operating Officer Helen, regional head for China Tina, and core technical experts. Their investigation confirmed that the anomaly was not a platform-wide security failure but an isolated case affecting a single user.
Bybit’s Official Response To The Apple Login ID Issue
Source: X (@Bybit_ZH)
Importantly, the user’s digital assets were never at risk of being compromised or lost. The security lapse revolved around an Apple ID-linked login process that triggered a temporary lock on withdrawals. After internal verification procedures and communication with the affected individual, Bybit restored account access and reinforced authentication protocols.
This situation reaffirmed Bybit’s proactive and user-centric approach. Their rapid engagement with the matter demonstrated a clear priority: user asset safety. The incident was managed transparently and efficiently, reinforcing trust among users and investors alike.
The broader market responded with understanding and optimism. Notably, Bybit’s swift response was praised by many, emphasizing how user access was restored with minimal disruption. The praise highlighted the platform’s efficiency in incident management.
Moreover, the community acknowledged the fact that this incident didn’t evolve into a systemic issue. No other users were affected, and the problem was resolved within a short window, showcasing the platform’s readiness to act quickly and effectively.
Bybit previously suffered a major hack in February 2025, resulting in a loss of approximately $1.4 billion, a stark contrast to this incident, where no user funds were lost. That breach had forced Bybit to reevaluate and overhaul its security infrastructure.
Bybit CEO Referring To A Hacking Incident In February 2025
Source: X (@benbybit)
Today, the company’s readiness in handling even isolated user anomalies shows the payoff from those improvements. Bybit appears to have learned from the past and applied those lessons swiftly to prevent any recurrence on a large scale.
Security experts have weighed in, noting that the company’s ability to contain this issue and restore access without external damages indicates a maturing security architecture. There was no systemic flaw or data compromise, just a single-user login inconsistency likely related to third-party authentication via Apple ID.
Bybit’s recent handling of this login-related concern also highlights the importance of continuous platform monitoring. While external login services like Apple ID offer convenience, they can sometimes introduce unforeseen vulnerabilities. Recognizing this, Bybit has upgraded user access verification steps and layered in additional security measures to prevent any disruption of services.
Crypto trading platforms operate under the constant threat of hacks, social engineering, and system bugs. The current case, while limited in scope, exemplifies the importance of having internal teams prepared for any kind of anomaly. Bybit’s ability to recover quickly, protect user funds, and maintain system-wide stability is now seen as a benchmark for others in the space.
For crypto traders and long-term investors alike, this incident serves as both a caution and a comfort. While vulnerabilities can arise, especially when integrating with third-party login services, the real takeaway is how platforms like Bybit choose to handle them. Fast action, transparent updates, and robust follow-ups can make all the difference between a PR disaster and a show of organizational strength.
Users are encouraged to remain vigilant by enabling two-factor authentication (2FA), using strong, unique passwords, and reporting any irregular activity without delay.
The May 18th Apple ID login anomaly marks a turning point in Bybit’s evolving security strategy. With no funds lost and platform stability preserved, the incident stands as proof that the company is better prepared than ever before to tackle disruptions.
Bybit’s decisive action not only protected one user but sent a reassuring message to the entire trading community: the lessons from past breaches have been learned, and user security is now non-negotiable.
Subscribe to stay informed and receive latest updates on the latest happenings in the crypto world!

Content Strategist
Subscribe to stay informed and receive latest updates on the latest happenings in the crypto world!
 Figure Heloc(FIGR_HELOC)$1.030.00%
Figure Heloc(FIGR_HELOC)$1.030.00% Wrapped stETH(WSTETH)$3,569.44-0.88%
Wrapped stETH(WSTETH)$3,569.44-0.88% Wrapped eETH(WEETH)$3,165.46-0.88%
Wrapped eETH(WEETH)$3,165.46-0.88% USDS(USDS)$1.000.00%
USDS(USDS)$1.000.00% Binance Bridged USDT (BNB Smart Chain)(BSC-USD)$1.000.04%
Binance Bridged USDT (BNB Smart Chain)(BSC-USD)$1.000.04% Coinbase Wrapped BTC(CBBTC)$88,094.00-0.53%
Coinbase Wrapped BTC(CBBTC)$88,094.00-0.53% WETH(WETH)$2,913.36-0.89%
WETH(WETH)$2,913.36-0.89% Ethena USDe(USDE)$1.00-0.01%
Ethena USDe(USDE)$1.00-0.01% Canton(CC)$0.149335-2.53%
Canton(CC)$0.149335-2.53% Hyperliquid(HYPE)$22.26-2.92%
Hyperliquid(HYPE)$22.26-2.92% USD1(USD1)$1.00-0.02%
USD1(USD1)$1.00-0.02% USDT0(USDT0)$1.000.00%
USDT0(USDT0)$1.000.00% World Liberty Financial(WLFI)$0.163241-6.57%
World Liberty Financial(WLFI)$0.163241-6.57% sUSDS(SUSDS)$1.08-0.29%
sUSDS(SUSDS)$1.08-0.29% Ethena Staked USDe(SUSDE)$1.220.08%
Ethena Staked USDe(SUSDE)$1.220.08% Rain(RAIN)$0.009663-3.23%
Rain(RAIN)$0.009663-3.23% MemeCore(M)$1.62-0.88%
MemeCore(M)$1.62-0.88%