
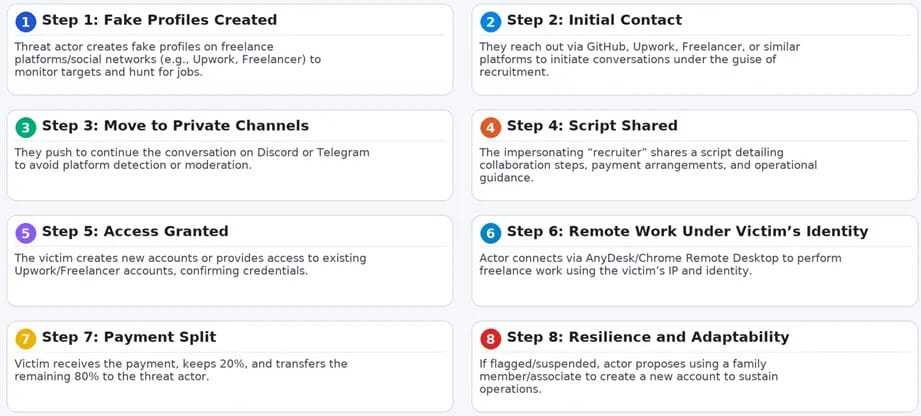
North Korean hackers are exploiting freelancers as identity proxies to access remote jobs.
Victims unknowingly provide verified accounts and domestic IP addresses, making the hackers appear legitimate.
Some participants are complicit, running “laptop farms” for profit.
Recruits often come from vulnerable or low-income backgrounds.
Remote access requests are the clearest sign of a scam.
According to cybersecurity expert Heiner García of Telefónica, North Korean operatives are contacting freelancers and job seekers online before moving conversations to encrypted platforms such as Telegram or Discord.
There, they coach recruits on how to set up remote access tools like AnyDesk or Chrome Remote Desktop.
The Hackers’ Tried-And-Tested Recruitment Process
Source: Heiner García/SEAL
Once access is granted, operatives work behind these verified profiles, performing technical tasks, applying for projects, and collecting payments, all under someone else’s identity.
The freelancer typically receives only 20% of the earnings, while the rest is funneled back to North Korea through cryptocurrencies or traditional bank transfers.
This approach helps North Korean hackers sidestep the digital barriers that platforms use to detect high-risk IP addresses and VPN usage.
Since the connection appears to originate from a legitimate, verified user in a safe location, the operatives blend seamlessly into the global freelance workforce.
Earlier this year, García and Cointelegraph set up a dummy crypto startup to investigate the scheme.
They interacted with a supposed Japanese candidate who abruptly ended a call when asked to speak Japanese. Later, the same person asked García to buy a computer and provide remote access, a now-familiar tactic among North Korean IT operatives.
Further analysis revealed recycled onboarding presentations, recruitment scripts, and ID documents, all reused across multiple fake freelancer profiles.
García explained:
“They install AnyDesk or Chrome Remote Desktop and work from the victim’s machine so the platform sees a domestic IP. The freelancers often think it’s a subcontracting arrangement, they don’t realize they’re being exploited.”
Several high-profile arrests in the United States confirm how deep this problem runs.
In August 2024, Matthew Isaac Knoot of Nashville was arrested for operating a “laptop farm” that helped North Korean IT workers appear as U.S.-based freelancers.
In Arizona, Christina Marie Chapman received an eight-year prison sentence for a similar operation that processed more than $17 million on behalf of North Korean actors.

Chapman’s Laptop Farm Duped More Than 300 US Companies
Source: Office of Public Affairs
These schemes tricked hundreds of U.S. companies, proving that even reputable platforms can be manipulated when hackers operate through legitimate accounts.
North Korean cyber recruiters are not just looking for any freelancer, they’re seeking economically vulnerable individuals who may overlook red flags.
García’s research uncovered emails targeting users from Ukraine, Southeast Asia, and low-income regions, including attempts to recruit people with disabilities.
García said:
“They target low-income people. They target vulnerable people. They even approach individuals with disabilities, promising easy remote income.”
This manipulation aligns with North Korea’s long-standing goal of using cyber operations to fund its weapons and missile programs, according to the United Nations.
While cryptocurrency theft remains a cornerstone of North Korean cybercrime, García’s findings show the strategy has expanded.
Operatives have used stolen or borrowed identities to take on projects in architecture, design, and customer support, even delivering legitimate work.
Some operatives now request direct bank payments, not just crypto transfers. This shift shows how deeply integrated their methods have become in both digital and traditional financial systems.
Even as platforms like Upwork and Freelancer tighten verification standards, North Korean hackers continue to exploit human loopholes.
When an account is flagged or suspended, the operatives simply move on, sometimes asking the same freelancer to recruit family members and create new accounts.
The challenge is that every signal looks legitimate:
The identity belongs to a real person.
The internet connection is local.
The paperwork checks out.
By the time suspicious behavior surfaces, the hackers have already moved on to new accounts and fresh victims.
The biggest warning sign is any request to install remote-access software or share control of your device. No legitimate employer or client needs direct access to your computer or account.
Rule of thumb: If someone asks to “work from your account,” they are not hiring you, they are using you.
They use freelancers’ verified identities and computers to bypass geographic restrictions and earn money through remote jobs, laundering funds into North Korea.
Most initial contact happens through legitimate freelance sites like Upwork, followed by chats on Telegram or Discord.
Everything from IT and crypto projects to architecture and customer support, anything that can generate foreign income.
Never share your computer, install remote desktop software for clients, or let anyone use your verified accounts. Report suspicious requests immediately to the platform.
Subscribe to stay informed and receive latest updates on the latest happenings in the crypto world!

Content Strategist
Subscribe to stay informed and receive latest updates on the latest happenings in the crypto world!
 Figure Heloc(FIGR_HELOC)$1.031.10%
Figure Heloc(FIGR_HELOC)$1.031.10% Wrapped stETH(WSTETH)$3,577.390.08%
Wrapped stETH(WSTETH)$3,577.390.08% Wrapped eETH(WEETH)$3,172.440.06%
Wrapped eETH(WEETH)$3,172.440.06% USDS(USDS)$1.000.00%
USDS(USDS)$1.000.00% Binance Bridged USDT (BNB Smart Chain)(BSC-USD)$1.00-0.04%
Binance Bridged USDT (BNB Smart Chain)(BSC-USD)$1.00-0.04% Coinbase Wrapped BTC(CBBTC)$87,742.00-0.89%
Coinbase Wrapped BTC(CBBTC)$87,742.00-0.89% WETH(WETH)$2,920.15-0.13%
WETH(WETH)$2,920.15-0.13% Ethena USDe(USDE)$1.000.02%
Ethena USDe(USDE)$1.000.02% Hyperliquid(HYPE)$27.5621.27%
Hyperliquid(HYPE)$27.5621.27% Canton(CC)$0.1525920.57%
Canton(CC)$0.1525920.57% USD1(USD1)$1.000.04%
USD1(USD1)$1.000.04% USDT0(USDT0)$1.000.14%
USDT0(USDT0)$1.000.14% World Liberty Financial(WLFI)$0.156815-0.51%
World Liberty Financial(WLFI)$0.156815-0.51% sUSDS(SUSDS)$1.090.14%
sUSDS(SUSDS)$1.090.14% Ethena Staked USDe(SUSDE)$1.220.07%
Ethena Staked USDe(SUSDE)$1.220.07% Rain(RAIN)$0.0100435.10%
Rain(RAIN)$0.0100435.10% MemeCore(M)$1.54-4.86%
MemeCore(M)$1.54-4.86%